1000 FAQs, 500 tutorials and explanatory videos. Here, there are only solutions!
Redirect web traffic to a specific port
This guide covers redirecting web traffic to a specific port, including when using a dedicated IP and a specific web application (such as Node or Varnish, for example).
Prerequisites
- Add a site to your hosting.
- Install
HAProxyon the Cloud Server.
Redirect web traffic to a specific port
By default, on the Cloud Server, web traffic is sent to Apache. To send requests to a Node script or another service (provided it "listens" on a port between 4000 and 4009), you need to go through HAProxy.
This applies in particular to Express, Socket.IO, Meteor.js, Nuxt.js, Django, Flask, Ruby on Rails, even possibly Java (J2E), etc.
To do this, you need to ensure that the service is listening on a port between 4000 and 4009 (especially with server.listen(4000) for Express or a basic Node HTTP server, but depending on the type of project by other means, a configuration file, in the code or otherwise) and on all interfaces (0.0.0.0).
It will also be necessary to configure HAProxy as in the example below:
- Click here to access the management of your Cloud Server on the Infomaniak Manager (need help?).
- Click directly on the name assigned to the Cloud Server in question.
- Click on Fast installer in the left sidebar.
- Click on the action menu ⋮ located to the right of
HAProxy. - Click on Configure:
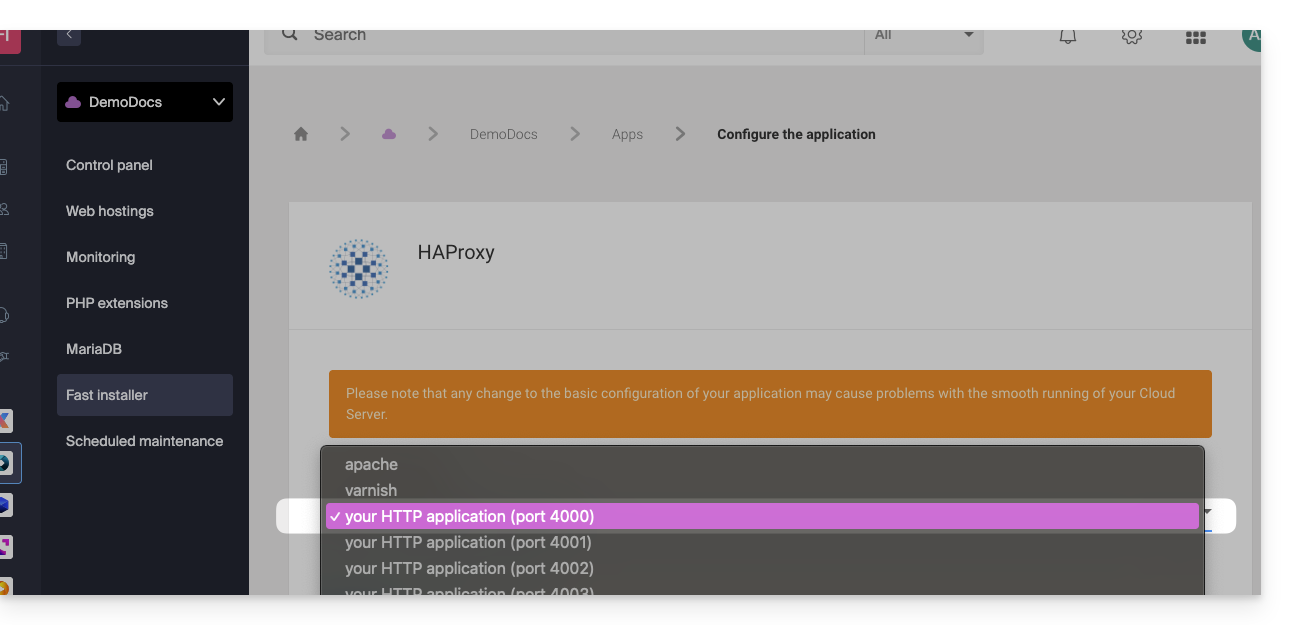
- Choose the desired information and save:
Retrieving the source IP of a request
When you redirect web traffic to your web application, the processing of requests changes and the request is first received by a reverse proxy (local to the server) which then forwards the request to the chosen port. Thus, due to the transfer of the request, the methods usually used to retrieve the visitor's IP will give the IP of the reverse proxy instead of that of the visitor.
Thus, to retrieve the real source IP of the visitor in these cases, you need to consult an HTTP header named X-Forwarded-For, which will contain the source IPs accumulated during each redirection. This header will therefore contain last the original IP address of the client, allowing the real visitor to be identified.
Warning: It is important to note that HTTP headers can be manipulated, which presents security risks. To minimize these risks, it is recommended to verify that the request comes from a trusted server before trusting the content of the header X-Forwarded-For. This verification may involve ensuring that the request was transmitted by a trusted intermediary server, identified by a predefined list of IP addresses. In the case where the site uses a dedicated IP, the trusted servers are:
- 83.166.133.15
- 83.166.133.17
- 83.166.133.16
- 84.16.92.5
- 84.16.92.43
- 10.2.32.255
- 10.2.34.164

